Ottawa, Ontario, September 23, 2024 – Quantropi is excited to announce it has partnered with Palo Alto Networks to bring its QiSpace™ PPK (Post-Quantum Preshared Keys) Generator to customers. This Palo Alto Networks validated Partner solution provides an elevated security posture protecting IPSec VPN traffic against “Harvest Now, Decrypt Later” attacks posed by quantum computing. QiSpace™ PPK Generator is an RFC 8784 standard compliant solution which provides immediate protection independent of post-quantum cryptography (PQC) standards.
Today’s Challenge
Organizations rely on site-to-site IPSec VPN security to protect their critical data. However, threat actors are storing encrypted communications and data today in order to decrypt them in the future using quantum computing or other advanced capabilities with an attack method called “Harvest Now, Decrypt Later”. To counter this attack vector, IPSec VPNs are beginning to incorporate new NIST PQC algorithms and hybrids, but this approach alone may not be sufficient.
It will take some time before fully approved FIPS-validated software packages with NIST PQC algorithms are available. In addition, the new algorithms do not have the same decades of vetting duration as the classic algorithms in use today.
According to Michael Redding, Quantropi CTO:
An immediate/complementary solution such as Post-quantum Preshared Keys is vital to protect critical data and communications and provides a “defense in depth” approach to further mitigate risks
– Michael Redding
RFC 8784 – A Standard for Quantum-Secure IPSec VPNs
The IETF RFC 8784 standard provides a mechanism to create quantum-secure IPSec VPN connections and is recommended by several government agencies, including NIAP, the NSA, and the German Federal Office for Information Security. It uses Post-quantum Preshared Keys (PPKs) that are shared by an out of band mechanism. The PPKs are “mixed” with the classic keys from the key exchange process and the resulting mixed keys are used to encrypt communications. These mixed keys are secure against Shor’s algorithm running on a quantum computer and other advanced attacks targeting the key exchange process. RFC 8784 protects IPSec VPNs against “Harvest Now, Decrypt Later” and is an immediate low-risk solution to harden communication security, that is independent of upgrading to PQC algorithms.
According to Palo Alto Networks Sr. Principal Product Manager, Philip Kwan:
Implementing Post-quantum Preshared Keys as defined by RFC 8784 for IPSec VPNs is by far the easiest way to move to a post-quantum capability.
– Philip Kwan
The RFC 8784 standard is fully supported and available today in Palo Alto Networks solutions and will immediately harden VPNs to a post-quantum posture.
Introducing Quantropi’s QiSpace™ PPK Generator
The QiSpace™ PPK Generator is a browser extension that can be installed from major App Stores including Chrome, Edge, and Firefox. The QiSpace™ PPK Generator is powered by Quantropi’s global quantum entropy generation and distribution network and can generate PPKs between 16-64 bytes that are securely delivered to the browser using AES-256 payload encryption.
PPKs should be strong random secrets that cannot be easily predicted. Therefore, the strongest PPKs need to be generated from truly random processes such as in quantum random number generators (QRNGs). These QRNG-based PPKs cannot be predicted algorithmically and are not subject to attacks from quantum computing or other advanced methods such as AI used with malicious intent.
Quantropi’s highly scalable quantum entropy generation and distribution network uses a heterogeneous portfolio of QRNGs from industry-leading vendors for maximum entropy diversity. Entropy quality is validated using a robust set of industry-standard statistical testing tools with audit reporting available.
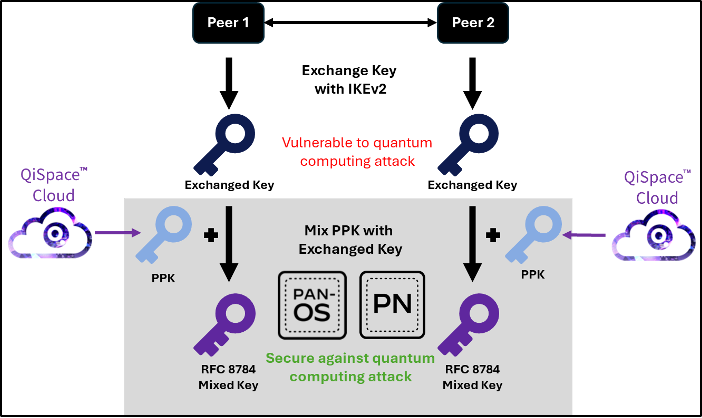
PPK Generator Now Supported on Palo Alto Networks NGFWs
Palo Alto Networks Next-Generation Firewalls (NGFWs) offer a prevention-focused architecture that is easy to deploy and operate. Beginning in PAN-OS 11.1, support has been added for RFC 8784 to enable key mixing with PPKs for post-quantum security in IPSec VPNs. QiSpace™ PPK Generator integrates seamlessly with these NGFWs and can be accessed directly from the NGFW configuration screen with no rekeying or copy/paste required. Currently, up to 10 unique PPKs can be configured for each IKE Gateway Profile.
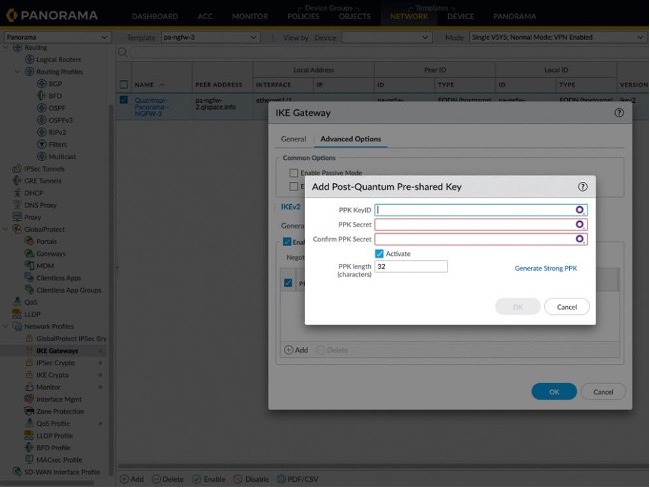
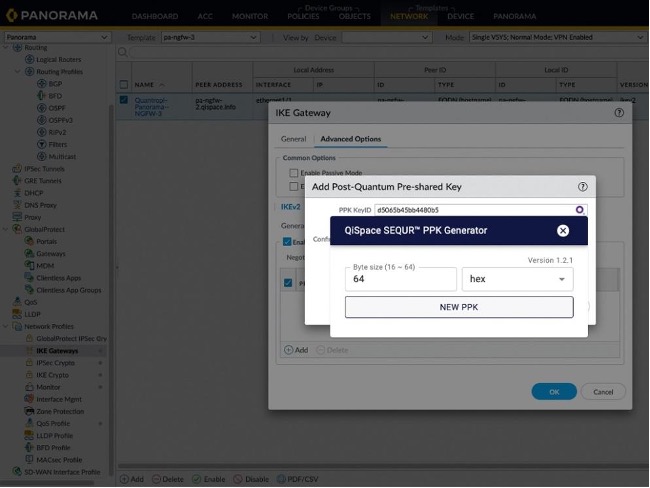
For customers that do not use Panorama for central management, the extension allows them to consistently configure the same set of PPKs for multiple NGFWs. For Panorama customers, with just a few clicks the extension can configure 10’s to 1000’s of NGFWs to ensure full interoperability between NGFWs.
Benefits of Integration with Quantropi’s PPK Generator
The Palo Alto Networks and Quantropi integration hardens customer IPSec VPN deployments, reduces harvesting attack windows, and secures against future advanced cryptographic attacks.
- Standards-based solution that is approved by world governments.
- Quantropi’s PPK solution improves the security provided by RFC 8784 by mixing PAN-OS’s IPSec VPN encryption key with quantum-generated truly random PPKs.
- Truly random PPKs cannot be algorithmically predicted, protecting against harvesting attacks from rapidly advancing AI and quantum technology.
- Setup and configuration is simple and straightforward on any Chromium browser that can be used to configure PAN-OS firewalls (including Panorama).
PPK Sovereignty
Quantropi’s three-tier architecture provides customers with protection, privacy and PPK sovereignty.
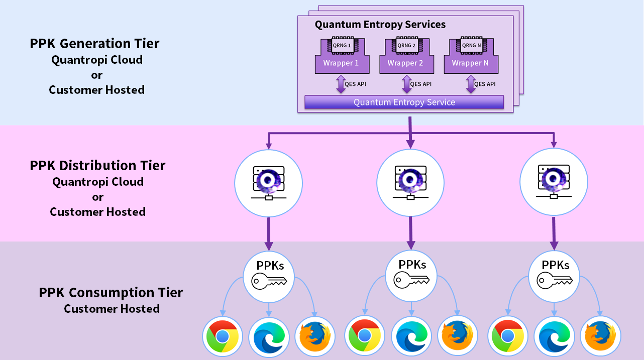
- PPK Generation Tier – Quantropi or customer-hosted cloud tier that uses FIPS-compliant, best-of-breed QRNG hardware devices to generate truly random entropy streams for PPK creation.
- PPK Distribution Tier – Customer-hosted containerized application used as a caching and distribution point for PPKs inside the customer network.
- PPK Consumption Tier – Browser extension endpoint used to receive PPKs for firewall configuration.
The customer-hosted Distribution Tier is a security boundary that keeps critical security information private to the customer including details about what endpoints are receiving PPKs, PPK consumption volume, and knowledge of the actual PPK itself.
PPK Transmission Security
The PPK is delivered quantum securely to the browser across all three architecture tiers using three mechanisms.
- The network transport is protected using TLS1.3. Customers have the option to use classic, NIST PQC, or PQC hybrid algorithms.
- The PPK payload is encrypted using a combination of AES-256 and a 1024-bit quantum-safe symmetric algorithm. Combined with transport security, this is a FIPS-compliant configuration for defense in depth.
- The PPK is “privatized” using a one-time pad. This means that at the Distribution Tier, the PPK is reset or scrambled to an entirely new, completely random value which protects against injection attacks.
“Harvest now, decrypt later” attacks are becoming more prevalent and the pace of advancements in AI and Quantum Computing technologies is accelerating. It is important for organizations to begin implementing post-quantum security now on the NFGWs and IPSec VPNs that they rely on to secure their data and communications.
RFC 8784 provides a standards-based mechanism to create quantum-secure IPSec VPN connections by key mixing with PPKs. The QiSpace™ PPK Generator is a Palo Alto Networks validated partner solution that seamlessly integrates with NGFWs running PAN-OS 11.1+.
Ready to enable post-quantum on PAN-OS? Sign up for a trial of the QiSpace™ PPK Generator now!
Want to learn more? Check out these pages:
QiSpace™ PPK Generator for Palo Alto Networks NGFWs.


